Data Masking Services
Data is the most essential asset of your organization. It might consist of valuable and sensitive information about your critical business operation. So, it must not be exposed to those who shouldn’t have access to it. Protect it with our data masking services. We help de-identify personally identifiable information (PII) following all data protection regulations.
25,000+
Projects
9+ years
Experience
ISO
Certified
15,000+
Satisfied Clients
99.99%
Accuracy
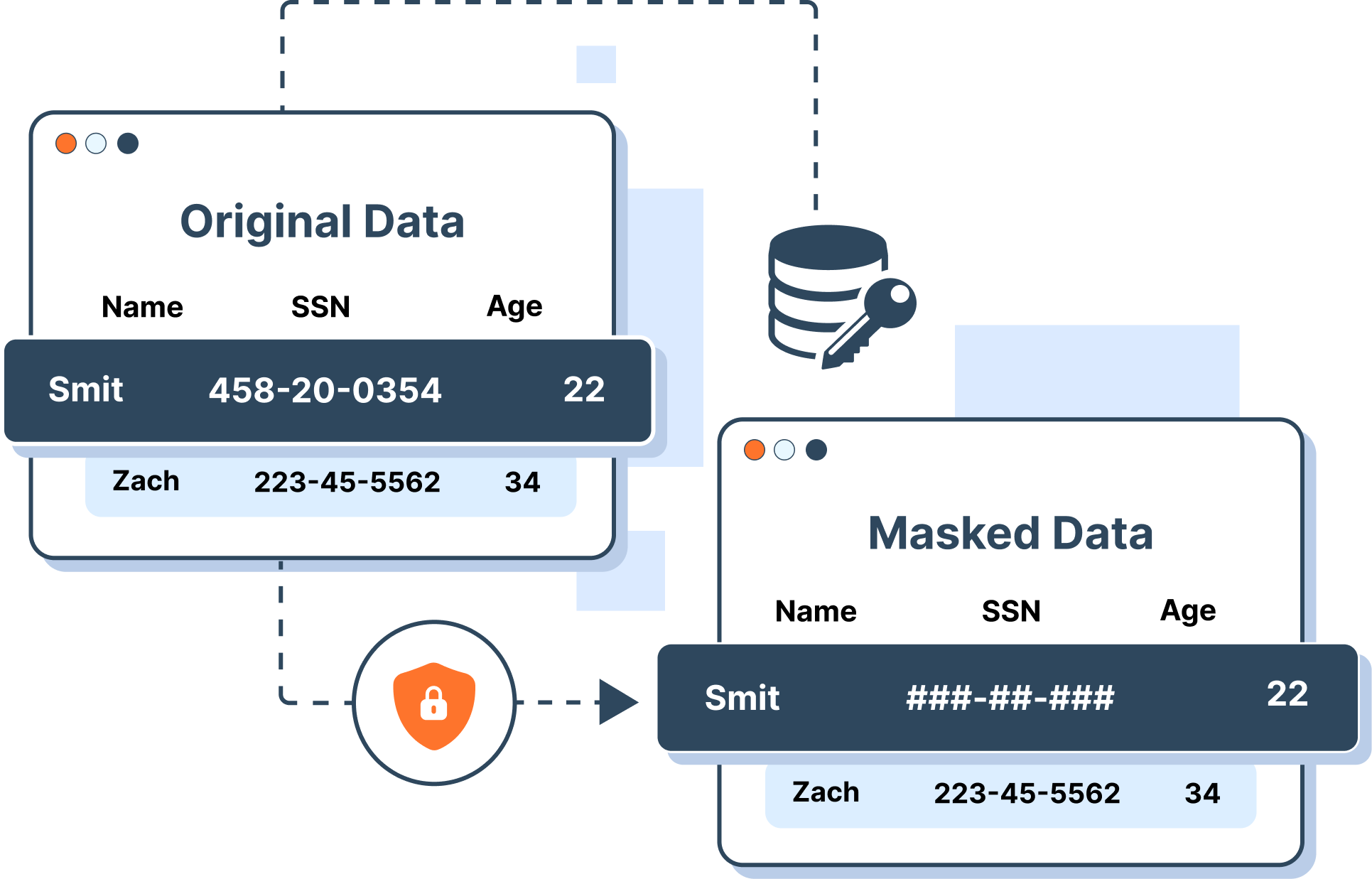
Hide Sensitive Values Without Changing the Core Information
Risk of data theft for customer data is high at the present time. As per industry estimates, more than 52% of customer PII got stolen in 2023 in various data breaching incidents. Thus, securing your customer data becomes your prior responsibility at this point. But do you know the chances of data theft increase when you share data without masking? It’s a huge risk. Don’t let it happen. Get our data masking services to de-identify PII accurately. Besides de-identifying information, we help you hide sensitive values when you share data.
With InputiX’s partnership, you can save the cost of hiring in-house data masking experts. Forget about hiring, you are not required to provide us with any sort of training regarding the work. Our experts are skilled and updated about the latest practices of data masking and can help you protect your data.
Data Masking Services We Work On
With the development of new technologies, new techniques are coming up for the working of data masking. We have included all the new techniques to protect your sensitive datasets with our diverse service offerings. Let’s check out how we can help you.
Static Data Masking
Data that does not change over time is getting masked with our static data masking procedures. We apply fixed sets of rules to mask the core static data. We replace sensitive data with alternative options permanently under this process.
Dynamic Data Masking
Based on your request, we will change our masking rules to hide your data values. Unlike the static, we create new rules to mask datasets. We can alter the data values for in-transit operation to ensure its security.
Deterministic Data Masking
Get data replaced in all the tables with the same masked value with our services. We follow the deterministic masking principle to hide your data from threats. Therefore, it provides you with more consistent and reliable alternatives for your actual databases.
On-the-Fly Data Masking
Eliminate the need to store masked information with our assistance. We apply on-the-fly data masking to alter your data without the need for storage. We measure specific requirements to mask your data using this technique.
Requirement of Masked Data
Masking data is a technique to create a fake but realistic replica of your original data. In this process, only the value of the data gets changed, not the format. The process changed the value to prevent reverse engineering. Masked data is used where a functional alternative is required, not the real data. At the time of software testing, demo sharing, etc. purposes, masking data becomes very relevant. With our data masking services, you don’t need to worry about hiding critical data values. We properly mask your data with all accurate measurements.
Pseudonymization
The EU GDPR (General Data Protection Regulations) coined the term “Pseudonymization” to recognize the data masking procedure. All types of masking including encryption come under this term that protects personal data.
Find your data that requires data masking protection
Techniques We Use For Data Masking
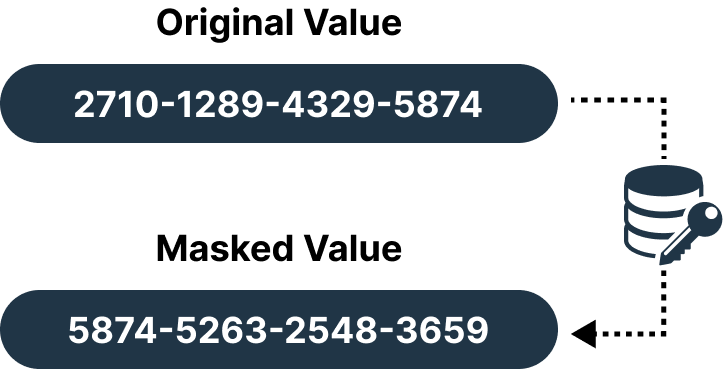
Randomization
Replace your sensitive data with randomly generated values that would not correlate with the original data. We replace names, addresses, and other personally identifiable information with randomly selected values or fictional inputs.
Substitution
Using algorithmic datasets, we generate fake names and numbers to replace your original sensitive data. Substitute masking involves replacing the original datasets with fictitious data. So we replace names and numbers with fictitious algorithmic datasets.
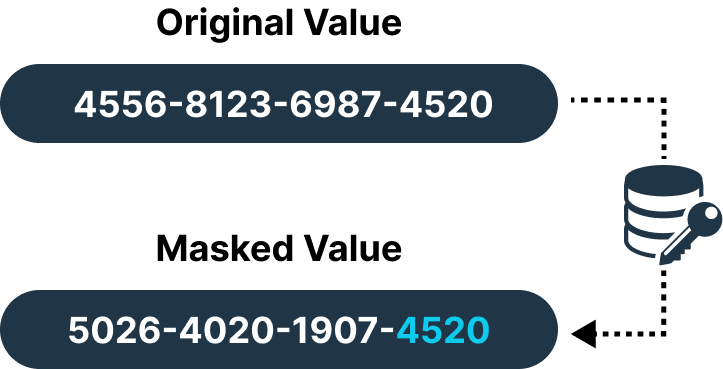
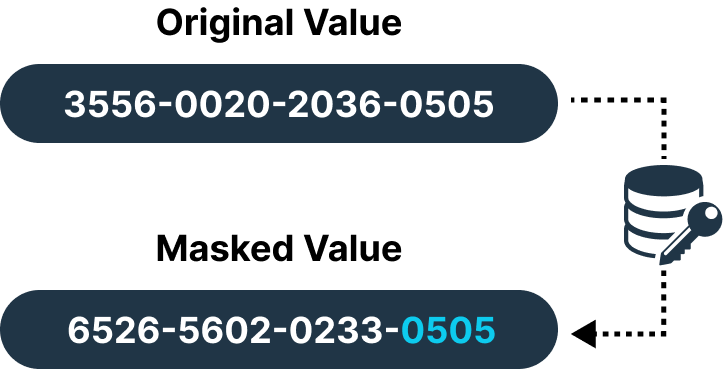
Shuffling
To make your individual records unidentifiable, we reorder the values within your database. The goal here is to preserve statistical properties and make your records unidentifiable. Shuffling is useful and predominantly used for preserving the relationships within datasets. (switching names and contact details of your customers’ data is shuffling)
Encryption
Deploying cryptographic algorithms, we encrypt sensitive data as a masking strategy. We make the data into an unreadable format, and only authorized users can decrypt the data using keys. This process of data masking adds a higher level of security to your sensitive data.
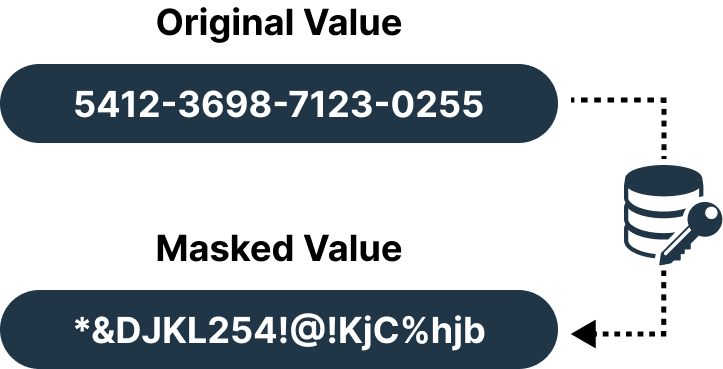
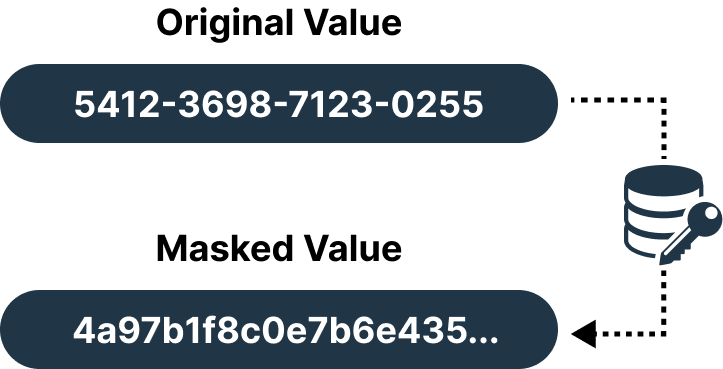
Hashing
Convert your data into a fixed-length string of characters using hashing techniques. Mainly, we consider applying this masking technique to mask passwords or any other highly sensitive information. Hashing helps verify data and adds new layers of security.
Tokenization
Replace your highly sensitive data with randomly generated tokens or reference values. Applying tokenization, we store the original data in a separate secure location and use the tokens as a substitute for processing or analysis. Tokenization minimizes the risks of exposing sensitive information.
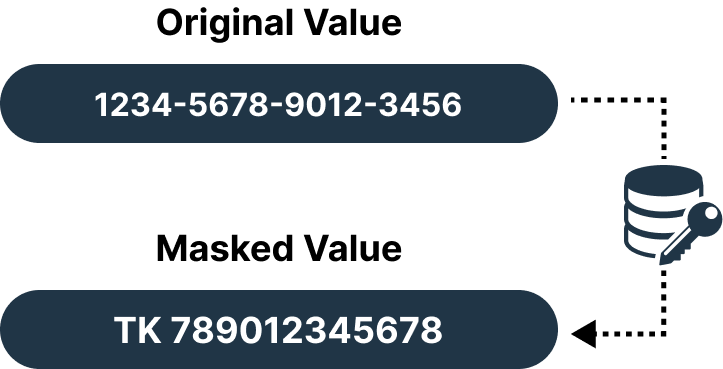
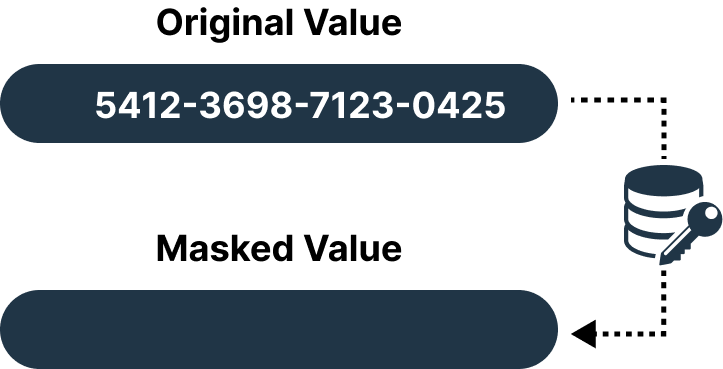
Nulling
Replace the sensitive data with null values or blank spaces using the nulling process. We conceal specific information, but we use the format and structure of the same data when creating null values. This masking technique suits when you want to use the structure of the data but not the values.
How do we solve data masking challenges?

Attribute Preservation
Masking tools must preserve the original data type, categories, and attributes. When a tool alters some vital part, like the demographic representation of customer data, it could impact analytics later. Hence, our team sharply tracks every procedure when we use any masking tools, especially when doing randomization or tokenization. We preserve attributes of the data before using any masking tool for better security.
Semantic Integrity
Masking adds fake value, but these values should reflect the original values and follow the business rules. For example, salary information along with national identification numbers is a predominant format. Therefore, we maintain semantic integrity when masking salary information. We add algorithmic national identification numbers, which make masked information look meaningful.

Uniqueness of Data
We always provide unique values to replace the original data. Because without uniqueness, key data fields may create potential conflict and inconsistencies. That’s why we maintain the uniqueness of data even if we add masked information to replace the original ones. Our data masking experts are well-trained in making the data values unique.

Existing Workflow Integration
Get a data masking workflow that smoothly integrates into your existing system, utilizing our data masking expertise. Our data masking experts adopt the new environment with minimal disruption. We strategically make all plans, collaborate with stakeholders, and address user concerns when we take over the data masking projects.
Alter Data By

Shuffle Characters
Word Substitution

Encryption

Replace numbers with special characters
InputiX is Popular for its Data Masking Services
A deep understanding of the relevancy of masked data is crucial to performing data masking work. We have been doing it for the last 9 years in this industry with all the necessary knowledge and skills. So, we can help you with any part of the data masking procedure and techniques.
Protect Sensitive Data, Apply Data Masking
Hide sensitive data with alternatives with the help of our data masking services. We do it with complete data protection. Sharing data without any protective layers is nothing but causing data threats. Masking the data is a way that can save your data from threats. We as a data entry service provider also help you in masking your datasets. Try our services and ensure the complete safety of your data. Fill out the form now to get our quote.
Client Experiences


With the help of InputiX, we added an extra layer security of the our banking operation. The expert team did not interrupt the regular banking challenges while performing the data mining work.
R. Jameson, Sr. Manager of a Californian Bank